SMotW #78: % of policies addressing viable risks

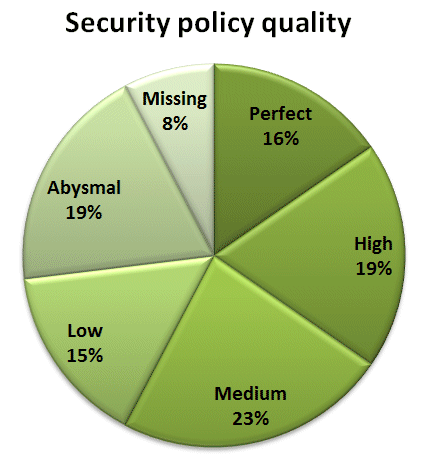
Security Metric of the Week #78: proportion of information security policies addressing genuine risks Writing policies is easy: writing policies that are relevant is harder than it sounds, and writing policies that are readable, fully implemented and straightforward to assess for compliance is harder still. This week's example metric is intended to highlight policies that are irrelevant or pointless, for example those that concern situations or risks that are remote ( extremely unlikely) in practice. If there is no conceivable combination of threat, vulnerability and business impact, there is little chance of an information security incident, hence a policy (or in fact any other form of control) is probably unnecessary. ACME rated the metric at 75% on the PRAGMATIC scale: P R A G M A T I C Score 65 76 91 73 83 77 70 61 78 75% There was some interest in us...