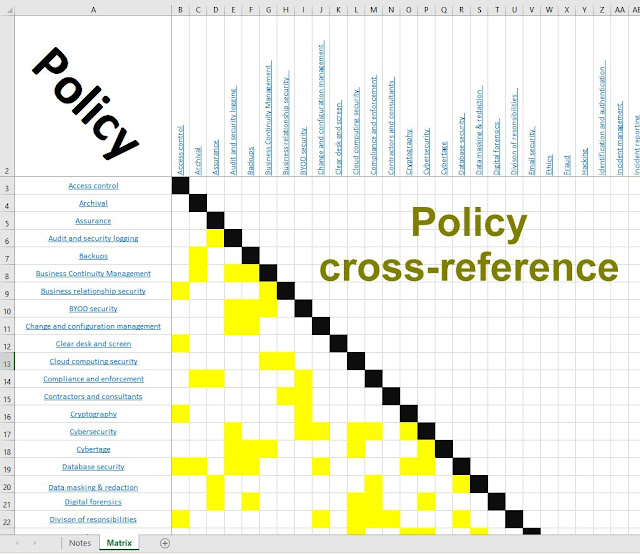
What are "information assets"?

Control 5.9 in ISO/IEC 27002:2022 recommends an inventory of information assets that should be “accurate, up to date, consistent and aligned with other inventories”. Fair enough, but what are ' information assets'? What, exactly, are we supposed to be inventorying? The standard refers repeatedly but enigmatically to "information and other associated assets" that an organisation’s I nformation S ecurity M anagement S ystem protects. The intended meaning of 'information asset' has been a bone of contention within ISO/IEC JTC 1/SC 27 for years , some experts and national bodies vehemently disagreeing with each other until, eventually, a fragile ceasefire was declared in order to move forward on the numerous standards projects that hinge on the term. Currently, '27002 provides a rather broad and unhelpful definition of "asset" as "anything that has value to the organisation" - paperclips, for instance, fall within the definition. D...