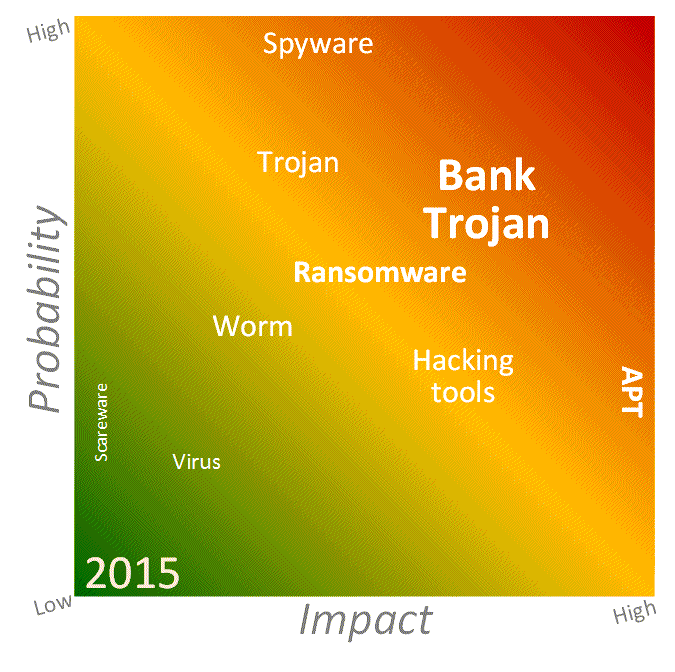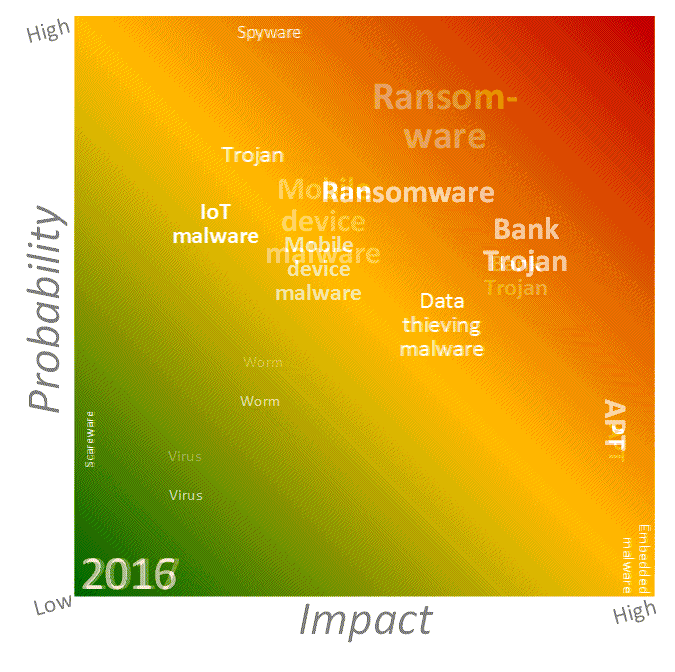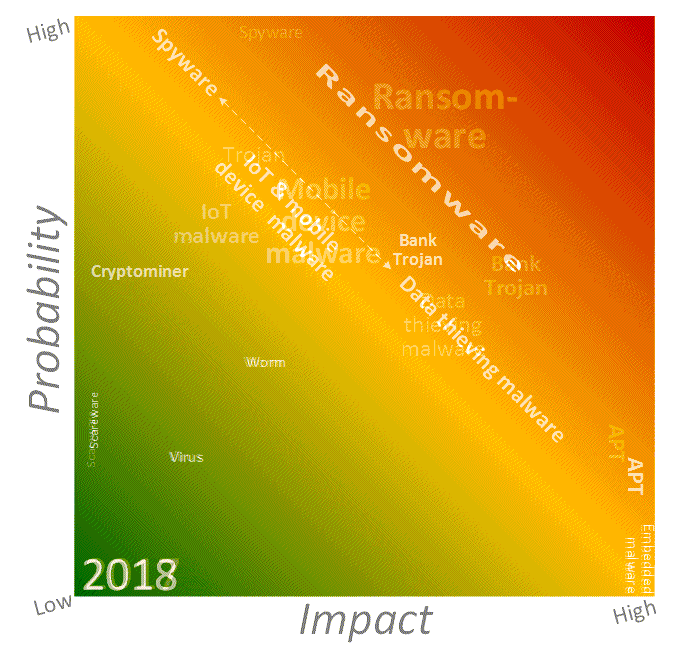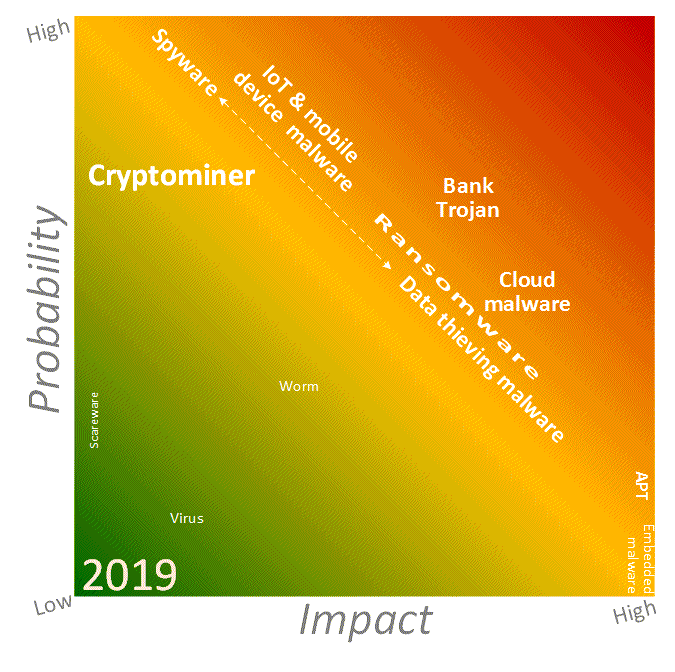
Yesterday's volcanic eruption on White Island is headline news around the globe, a tragedy that sadly resulted in several deaths, currently estimated at 13.
Also, yesterday in NZ there were roughly 90 other deaths (as there are every day), roughly two thirds of which were caused by cardiovascular diseases or cancer:

So, yesterday, the proportion of deaths in NZ caused by "Natural disasters" spiked from 0% to 13%. Today, it is likely to fall back to 0%.
"Natural disasters" will have caused roughly 0.04% of the ~33,500 deaths in NZ during 2019 ... but judging by the news media coverage today, you'd have thought NZ was a disaster zone, a lethal place - which indeed it is for ~33,500 of us every year. Very very few, though, expire under a hail of molten rock and cloud of noxious fumes, viewable in glorious Technicolor on social media.
Those 13 tourists who perished yesterday chose to see NZ's most active volcano up close, real close. You may be thinking "Ah but if they'd known it would erupt, they wouldn't have gone" ... but they did know it was a possibility: for at least some of the 13, that was the very reason they went. It's euphemistically called "adventure tourism". The possibility of death or serious injury is, perversely, part of the attraction, the thrill of it. Recent warnings from geologists about the increased threat of eruption on White Island would, I'm sure, have been carefully considered by the tourist companies involved, plus I guess they may have noticed changes in the amount of steam and sulfur lingering in the air. Tourists are explicitly warned about the dangers and instructed on the safety aspects. I gather one of the dead was a local, an employee of the tourist company. Aside perhaps from the geologists, it's hard to think of anyone more aware of the risk.
Having weighed-up the risks and rewards, the 13 enjoyed an amazing spectacle, doing the equivalent of 'clicking the go-away button' to dismiss computer security warnings despite facing, in their case, the ultimate impact. While I suspect their final moments would have been literally petrifying, hopefully the extra-special buzz leading up to it made it worthwhile. At that point, having made their decision to go, they were committed to their fate.
No doubt those who escaped the island alive will be thinking themselves lucky. They 'cheated death', coming as close as possible to being wiped-out ... and I'm sure they'll be telling everyone they can about it, some excitedly spreading the idea that near-death experiences are the ultimate thrill. The grieving relatives and friends of the dead, on the other hand, will have plummeted into the pit of despair, a very introspective and sad place. Some might be spreading the word that "adventure tourism" is lethal and crazy, but do you honestly think this incident will materially change the way it is promoted and advertised in future? Will "adventure tourism" and "extreme sports" operators go bust in short order?
Conceivably, some tourists decided not to take the fateful trip yesterday on safety grounds, or because they determined that it was "too expensive" and hence "not worth it". Although usually framed as a value judgment, to me that's a risk decision. Clearly they chose correctly, regardless of their analysis. The risk outweighed the benefits. I'd be interested to learn more about their thought processes.
So there we have it: ultimate impact or ultimate thrill. The uncertainty is part of the package, part of the attraction for some. It's something I've seldom seen discussed in relation to information risk, specifically, although risk-acceptance is part of the professional lexicon. There are legitimate business reasons for knowingly getting into risky situations. We advise and assist our corporate colleagues to identify and evaluate the risks, to reduce them where cost-effective and prepare to deal with incidents and disasters when they eventuate. Risk, incident, disaster, safety and business continuity management are all part of the same process. Risk avoidance is often a viable option, one that should not be simply dismissed out of hand. There's a reason that "wise old men" are old.