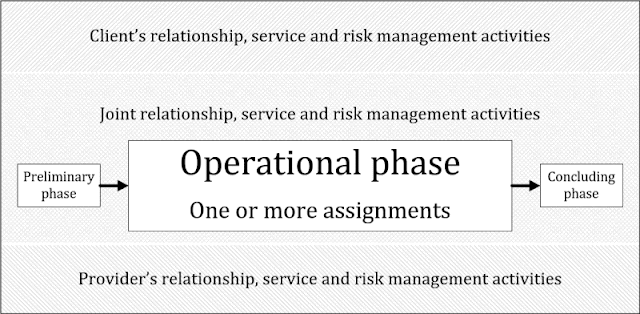
Professional services - concluding phase

Having introduced this blog series and covered information risks applicable to the preliminary and operational phases of a professional services engagement, it's time to cover the third and final phase when the engagement and business relationship comes to an end. Eventually, all relationships draw to a close. Professional services clients and providers go their separate ways, hopefully parting on good terms unless there were unresolved disagreements, issues or incidents (hinting at some information risks). It is worth considering what will/might happen at the end of a professional services engagement as early as the preliminary pre-contract phase. Some of the controls need to be predetermined and pre-agreed in order to avoid or mitigate potentially serious risks later-on. Straightforward in principle ... and yet easily neglected in the heady rush of getting the engagement going. This is not unlike a couple drawing up their "pre-nup" before a wedding, or a sensible organi...