The TEN controls ISO/IEC 27002 missed
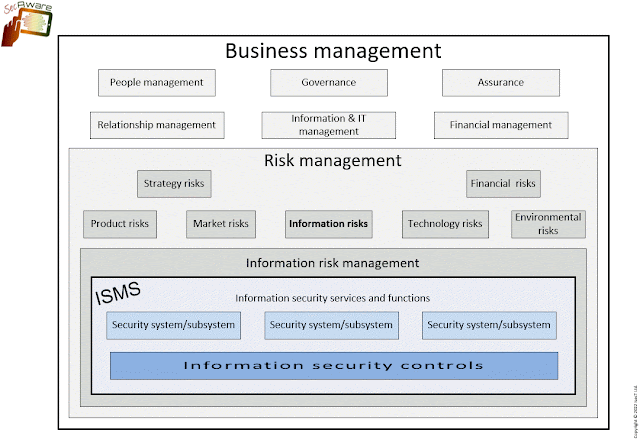
Despite the excellent work done to restructure and update the standard, I still feel some commonplace 'good practice' information security controls are either M issing I n A ction or inadequately covered by ISO/IEC 27002:2022 , these nine TEN for example: Business continuity controls, covering resilience, recovery and contingency aspects in general, not just in the IT security or IT domains. ISO 22301 is an excellent reference here, enabling organisations to identify, rationally evaluate and sensibly treat both high probability x low impact and low probability x high impact information risks (the orange zone on probability impact graphics), not just the obvious double-highs (the reds and flashing crimsons!). Therefore, '27002 could usefully introduce/summarise the approach and refer readers to '22301 and other sources for the details. Availability and integrity controls supporting/enabling the exploitation of high-quality, up-to-date, trustworthy business information a...


