ISO/IEC 27002 update
The newly-published third edition of ISO/IEC 27002 is a welcome update to the primary ISO27k controls catalogue (officially, a 'reference set of generic information security controls').
Aside from restructuring and generally updating the controls from the 2013 second edition, the committee (finally!) seized the opportunity to beef-up the coverage of information security for cloud computing with new control 5.23, plus ten other new controls, mostly in section 8 (technological controls):
- Configuration management (8.9) - concerns the need to manage security and other configuration details for [IT] hardware, software, [information] services and networks.
- Data leakage prevention (8.12) - DLP is required to protect sensitive information against unauthorized disclosure/extraction (theft, surveillance).
- Data masking (8.11) - in line with the organisation’s access control policy, plus other business requirements and compliance obligations, scurity controls are apropriate to mitigate the risk of disclosing sensitive personal and proprietary information.
- ICT readiness for business continuity (5.30) - organisations need to prepare themselves to handle serious incidents affecting/involving critical ICT e.g. through disaster recovery.
- Physical security monitoring (7.4) - intruder alarms, CCTV, guards etc. for business premises [such a basic, commonplace control that I can barely believe it was missing from the second edition ...].
- Information deletion (8.10) - at face value, another 'obvious' control: data should of course be deleted when no longer required to prevent unnecessary disclosure and for compliance reasons. The fine details, however, about how information gets deleted, matter in practice.
- Monitoring activities (8.16) - 'anomalies' on IT networks, systems and apps should be detected and responded to, to mitigate the associated risks.
- Secure coding (8.28) - software should be [designed and] coded securely, reducing the number and severity of exploitable vulnerabilities arising from [design flaws and] bugs. This control almost - but not quite - nailed the widely respected principle of 'secure by design'.
- Threat intelligence (5.7) - gathering relevant, actionable intelligence about threats to the organization's information, feeding it into the information risk management process.
- Web filtering (8.23) - limiting our access to inappropriate, unsavoury or plain risky websites is, apparently, an information security control important enough to warrant inclusion in the third edition.
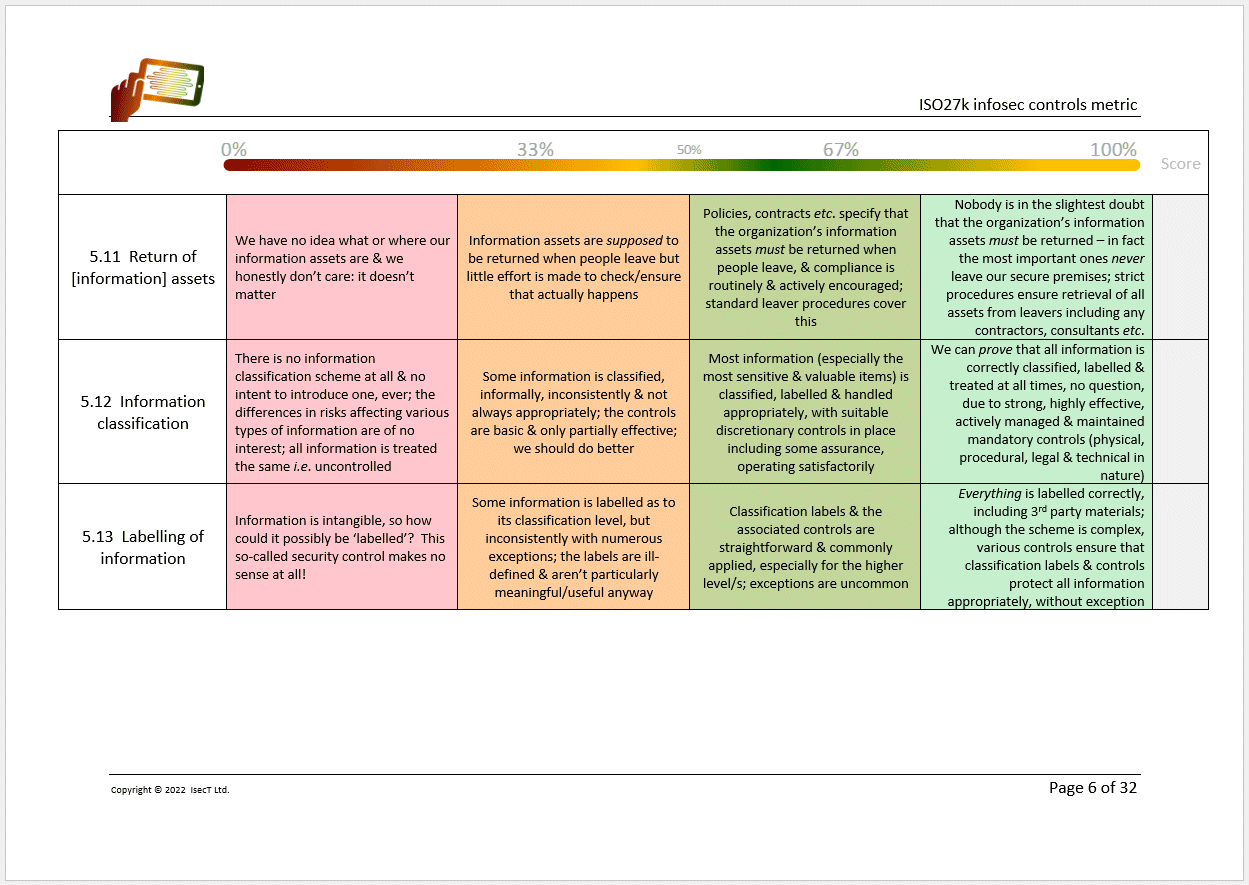
We've been busy updating the SecAware ISMS templates such as the detailed security controls maturity metric/checklist:
To supplement the extensive suite we already offer, we are currently finalising topic-specific policy templates on threat intelligence and data masking (details to follow).
The revised standard is weak on Internet of Things security - not surprising really given that the field is so immature, the IoT things proliferating so quickly and the technology so limited in terms of processing, storage and other capabilities, that information security controls are bound to be problematic. That said, there is a stack of work going on within SC 27 and other ISO committees, bringing the benefits of standardisation and shared good practices to IoT ... hopefully.